Kazi Mustafiz, October 06, 2022:
Cyber security experts have stated that the specific publication of a list of 29 organizations by the government’s Information and Communication Technology (ICT) Division as Critical Information Infrastructure (CII) has increased the risk for these organizations. Such actions from a crucial government body have reportedly stunned those involved.
A relevant government official claimed that neighboring countries like India, Nepal, and Malaysia similarly publish the specific names of organizations as CII, and that Bangladesh’s CII guidelines also state the same. However, a check of these three countries’ websites did not confirm his statement. Cyber security experts disregard his comment, stating there is no precedent anywhere in the world for directly publishing an organization’s name as CII. Instead, critical infrastructure is identified sector-wise, so that relevant parties are encouraged to strengthen necessary security measures.
Government Notification and Expert Reactions
On October 2, a gazette notification was issued by the Information and Communication Technology Division of the Ministry of Posts, Telecommunications and Information Technology. It stated that 29 organizations were declared as Critical Information Infrastructure under Section 15 of the Digital Security Act. These include institutions like Bangladesh Bank, four state-owned banks (Sonali, Rupali, Agrani, and Janata), the Securities and Exchange Commission, the Stock Exchange, and the National Board of Revenue (NBR).
The Reporter sought the opinions of at least five cyber security experts on this matter. Mohammad Iqbal Hossain, former President of the Dhaka Chapter of the Information Systems Audit and Control Association (ISACA), an international organization of IT professionals, and former Auditor General of the government, expressed surprise regarding the list of 29 organizations. He told DhakaTimes, “The names of organizations are not specifically published as Critical Information Infrastructure in this manner. This makes the organizations a target for cyber criminals, which further increases cyber security risks.”
An IT Chief from a private bank, who wished to remain anonymous, stated, “There is no rule anywhere in the world to publish specific organizational names as CII like this. It was a grave mistake for such an important government department to release this information publicly.” This expert added that even if a serious risk is detected in an organization, it can be privately informed so that necessary measures are taken. But publishing it publicly is inappropriate.
Banking Sector Concerns
In addition to Bangladesh Bank, the government notification also listed four state-owned banks. When asked about this, Syed Zahid Hossain, Chief Computer Network Engineer of Jamuna Bank’s IT Division, told DhakaTimes, “It was not right to mention it this way. If one has an illness, it’s not announced publicly; instead, efforts are made to cure it. Similarly, critical infrastructure risks should be mentioned sector-wise, not specifically.”
Tarek M Barkatullah, Director (CA Operation & Security) of the government’s Bangladesh Computer Council (BCC), and concurrently Director (Operation) of the Digital Security Agency (DSA), is directly involved with the publication of the list of 29 organizations. When asked about this, Tarek M Barkatullah stated, “The list of 29 organizations has been published as per the CII guidelines created in Bangladesh. Besides neighboring India, names of organizations are also published this way in Nepal and Malaysia.”
Another official from the ISACA Dhaka Chapter, who is the technology head of a private bank and wished to remain anonymous, told DhakaTimes, “This might primarily be due to a lack of understanding among relevant government officials. The names of organizations are not published as CII anywhere in this manner; rather, the sectors are mentioned.”
This cyber security expert emphasized that for sensitive issues like cyber security, it would be more fruitful to consult with relevant public and private stakeholders before taking any final steps.
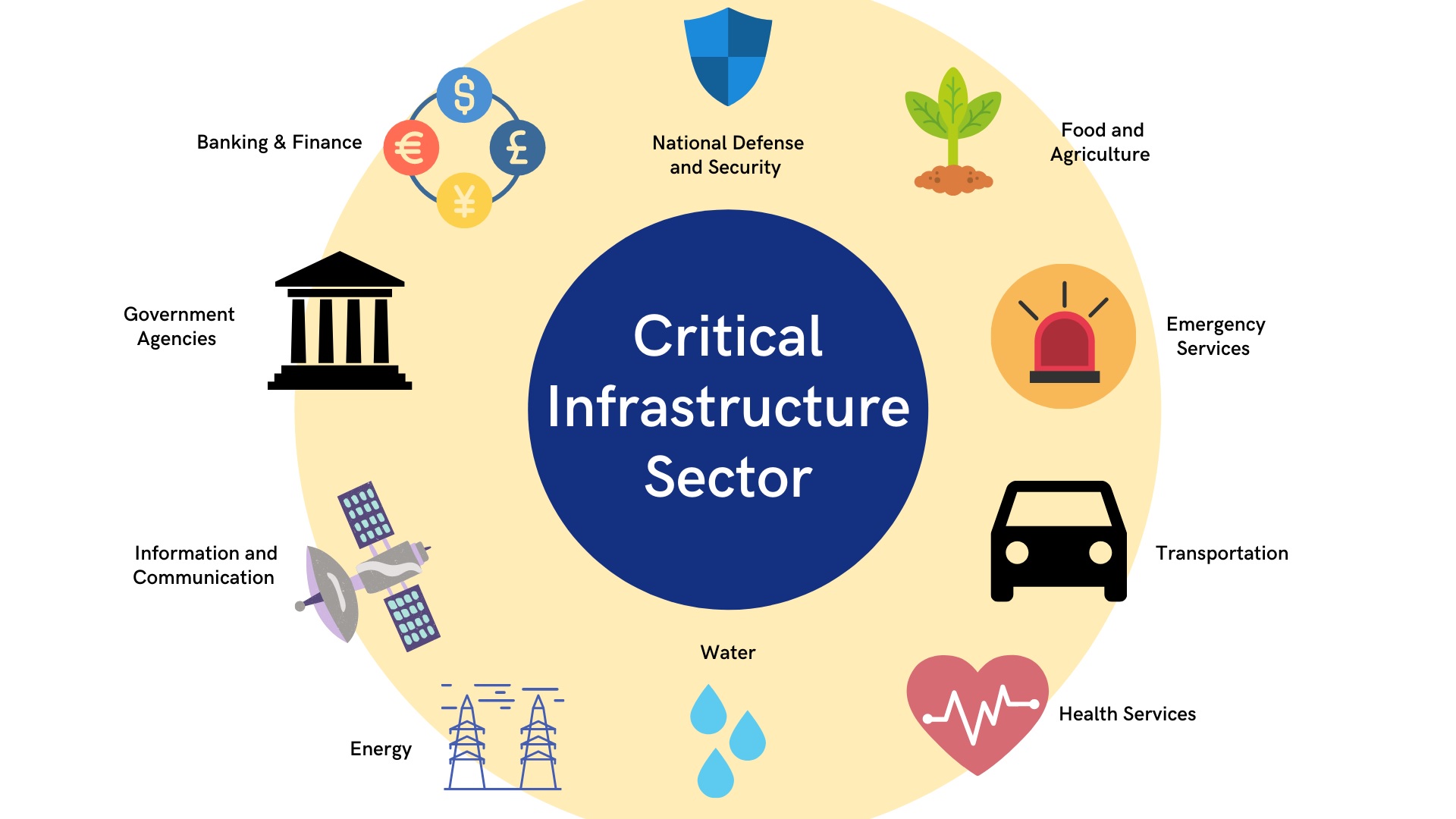
What Exactly is Critical Information Infrastructure?
Critical Information Infrastructure (CII), or Critical National Infrastructure (CNI), describes vital installations and their security, which are essential infrastructures for protecting the security of a society and its economy.
Critical infrastructure includes all assets, systems, and networks, both physical and virtual, that are necessary for a society’s economy, national public health, or security. Important infrastructure includes the food and agriculture sector, transportation systems (e.g., roads, railways, highways, airports), water supply systems, internet and mobile phone networks, public health institutions, energy (oil and gas), electrical utilities, financial services, telecommunications, defense, and much more. While critical infrastructure is similar in all countries due to basic living necessities, the infrastructure considered critical can vary according to a nation’s unique needs, resources, and level of development.
Necessity of Ensuring Critical Infrastructure Security
Critical infrastructure often incorporates Industrial Control Systems (ICS), including Supervisory Control and Data Acquisition (SCADA) systems, which are used to automate industrial processes in critical infrastructure industries. Cybercriminal attacks against SCADA and other industrial control systems are a serious concern. There is a risk of cyberattacks on critical systems such as transportation, oil and gas supply, electrical grids, the financial sector, and water supply. The connection and interdependence between infrastructure systems and sectors mean that if one or more functions fail or experience a blackout, there can be immediate negative impacts across multiple sectors. For example, in May 2021, cybercriminals launched a cyberattack on the Colonial Pipeline, which controls almost half of the gasoline, jet fuel, and diesel flowing along the East Coast. By seizing a password, cybercriminals took control of the largest fuel pipeline in the United States, severely disrupting fuel supplies on the East Coast.
The threat of cyberattacks against industrial control systems also has financial implications. Cybercriminals consistently target all types of IT-dependent management systems in critical infrastructure, including IT systems, OT (Operational Technology) systems, and IoT (Internet of Things), as their targets for attacks.
Information Gathering by Journalists and the Right to Information
Regarding the concern that the notification might create obstacles for journalists in collecting news or information under the Right to Information Act concerning the listed organizations, Tarek M Barkatullah stated that this is not relevant to the matter of critical infrastructure.
Others involved stated that according to the Right to Information Act, interested individuals must apply to the relevant organization following specific rules to obtain desired information. On the other hand, the Digital Security Act emphasizes the security of computer, software, and network systems within critical sectors.